Convey Your Personal Gadget (BYOD) tradition has reworked the way in which we work, providing comfort and suppleness.
Almost 67% of firms are switching to BYOD tradition.
The pattern, nevertheless, poses important dangers corresponding to:
- Knowledge breaches
- Knowledge loss or theft
- Compliance violations
- Malware and viruses
- Worker privateness issues
So, how can organizations guarantee security towards these dangers whereas encouraging BYOD tradition?
A BYOD administration resolution corresponding to Workstatus might assist companies to safeguard their knowledge whereas guaranteeing a seamless and safe BYOD surroundings.
Understanding BYOD
BYOD ( Convey Your Personal Gadget) is an organizational coverage that enables staff to make use of their units (corresponding to smartphones, tablets, or laptops) for work functions.
Listed here are some key factors to know about BYOD:
- Comfort and suppleness: BYOD presents staff the comfort of utilizing acquainted units, permitting them to work from anyplace and anytime.
- Elevated productiveness: Workers can use their most well-liked units, which regularly results in elevated effectivity and productiveness.
- Value financial savings: BYOD can scale back prices for organizations, as they don’t want to offer units for each worker.
- Gadget range: Workers can select units that go well with their preferences and desires, resulting in a various vary of units within the office.
- Coverage and tips: Organizations should set up clear BYOD insurance policies and tips to handle safety issues and guarantee correct system utilization.
Dangers and Challenges of BYOD
Convey Your Personal Gadget (BYOD) work tradition has its share of dangers and challenges.
Whereas BYOD presents comfort and suppleness, you should know the potential safety vulnerabilities and compliance points.
Listed here are some key dangers and challenges related to BYOD:
1. Knowledge breaches: BYOD comes with the danger of knowledge breaches, the place delicate firm data could also be accessed or stolen because of insufficient safety measures or compromised worker units.
- Lack of management over private units and their safety configurations will increase the potential for knowledge breaches
- Unauthorized entry to company networks by way of compromised private units can result in important knowledge leaks
2. Unauthorized entry: With out correct safety measures, private units used for work functions can grow to be targets for unauthorized entry, jeopardizing confidential data.
- Weak or simply guessed passwords can permit unauthorized people to entry delicate knowledge
- Misplaced or stolen units can fall into the unsuitable palms, leading to unauthorized entry to company assets
3. Compliance points: BYOD brings about compliance challenges, as organizations want to make sure that staff adhere to knowledge safety and privateness laws.
- Private units could not have the mandatory security measures or encryption protocols required for compliance
- Accessing delicate knowledge on private units can blur the road between private and work-related data, doubtlessly violating privateness laws
4. Malware and viruses: Private units could also be extra susceptible to malware and viruses, posing a risk to non-public and company knowledge.
- Workers could unknowingly obtain malicious purposes or go to unsafe web sites, resulting in malware infections
- Contaminated private units can act as a gateway for malware to unfold to company networks and compromise delicate knowledge
5. Worker privateness issues: Balancing knowledge safety with worker privateness is difficult in BYOD environments.
- Organizations should set up clear boundaries concerning knowledge entry and privateness rights on private units
- Monitoring worker units and actions could increase issues about privateness and private use of units
6. Gadget range and compatibility: With BYOD, staff use a variety of units, every with completely different working programs and configurations, which may pose compatibility and administration challenges.
- Supporting a number of system platforms and variations requires extra assets and experience
- Guaranteeing seamless integration with company programs and purposes throughout varied units will be complicated
Managing BYOD Dangers with Workstatus
Right here’s how Workstatus might help you with managing dangers related to BYOD:
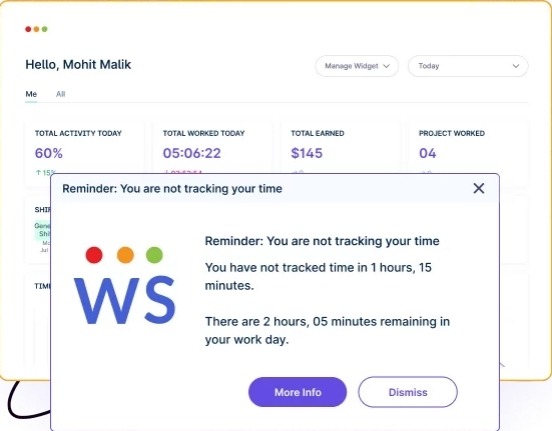
1. Stopping Time Tampering
With Workstatus, organizations can implement time monitoring and attendance options to forestall time tampering and guarantee correct worker reporting.
- Time monitoring capabilities permit staff to log their work hours transparently and stop unauthorized modifications
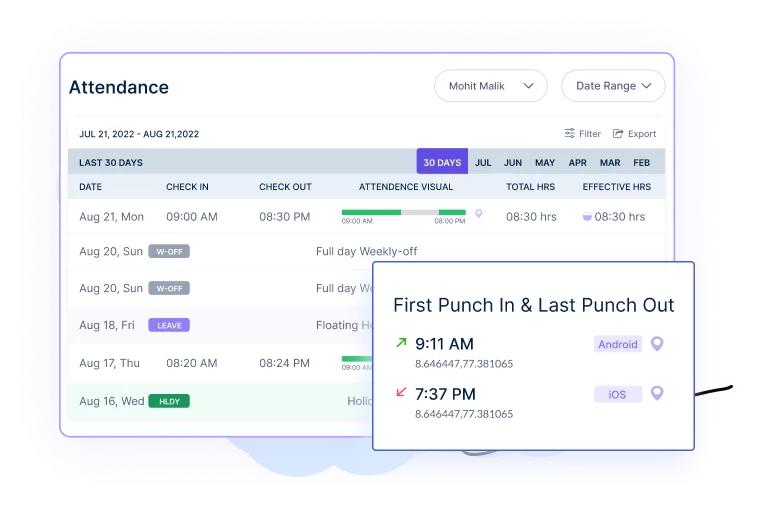

2. Figuring out Suspicious Conduct
Workstatus helps organizations detect and establish suspicious conduct which will point out potential safety threats or coverage violations.
- Consumer conduct analytics (UBA) capabilities like monitoring keyboard and mouse actions, productiveness monitoring, exercise tracker, and many others., analyze worker actions and flag uncommon patterns or deviations from regular conduct
- Worker monitoring might help you with the next analytics:
- Calculating time spent on apps and web sites
- Recording energetic screens
- Observe idle time
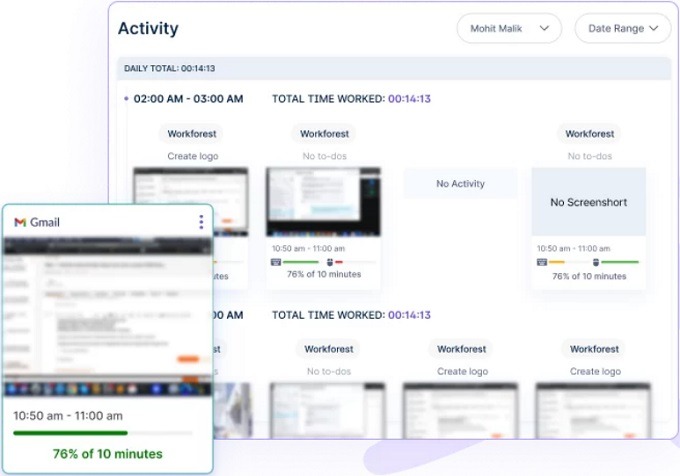
And it’ll ship alerts to directors concerning any potential safety dangers.
- Actual-time notifications permit immediate investigation and response to mitigate potential threats and stop knowledge breaches
3. Obtain Knowledge Experiences
Workstatus offers detailed knowledge stories that supply visibility into worker every day hours utilization, actions, and productiveness.
- Organizations can generate stories on worker exercise logs, together with exercise utilization, attendance historical past, and productiveness, to make sure adherence to knowledge safety laws
- Often downloading and analyzing knowledge stories helps ongoing danger evaluation and coverage refinement processes
- Experiences on worker conduct patterns allow firms to refine BYOD insurance policies, improve safety protocols, and supply focused coaching to staff

Some Case Research For You!
Learn the beneath infographics to know the way Workstatus helped firms develop a BYOD tradition.

These success tales present the constructive outcomes of Workstatus throughout a number of companies.
4. Finest Practices for Knowledge Safety
Implementing robust knowledge safety practices is essential to remove the dangers related to unauthorized entry and knowledge breaches.
Listed here are some finest practices to boost knowledge safety:
Encrypt Delicate Knowledge
- Make the most of encryption strategies to safeguard delicate knowledge each at relaxation and in transit
- Implement robust encryption algorithms and make sure that encryption keys are managed securely
Implement Robust Password Insurance policies
- Implement password insurance policies that require staff to create robust, distinctive passwords and repeatedly replace them
- Encourage the usage of password managers and keep away from password reuse throughout a number of accounts
Often Backup Knowledge
- Set up automated and common knowledge backup procedures to make sure knowledge availability and restoration within the occasion of knowledge loss or system failures
- Retailer backups securely, ideally off-site or in encrypted cloud storage
Monitor and Audit Knowledge
- Implement monitoring and auditing mechanisms to trace knowledge, detect anomalies, and establish unauthorized actions
- Often assessment audit logs to establish and reply to safety incidents promptly
Closing Ideas
Within the BYOD period, balancing comfort and knowledge safety is paramount for organizations.
Workstatus is a worthwhile device in attaining this equilibrium by empowering organizations to safeguard knowledge whereas maximizing the advantages of BYOD.
By embracing Workstatus, you’ll be able to guarantee a safe and environment friendly work surroundings for workers and shield worthwhile knowledge belongings.
FAQs
Ques. Is BYOD a safe possibility for my group?
Ans. BYOD will be safe if correct safety measures corresponding to encryption, robust passwords, and distant system administration are applied.
Options like Workstatus present the entire package to boost safety in a BYOD surroundings.
Ques. Can staff entry delicate knowledge on their units?
Ans. Sure, staff can entry delicate knowledge on their private units, however strict entry controls, encryption, and safe community connections are required to make sure knowledge safety.
Ques. How can Workstatus assist in managing BYOD dangers?
Ans. Workstatus presents options like worker monitoring, time tampering, and exercise stories, enabling firms to mitigate BYOD dangers, keep knowledge safety, and guarantee regulatory compliance.
Ques. Does Workstatus adjust to any knowledge certifications?
Ans. Sure, Workstatus complies with the next knowledge certifications:
- ISO 9001 High quality administration
- ISO 14001 Environmental administration
- ISO 22301 Safety and resilience
- ISO 27001 Data safety administration
- ISO 50001 Vitality administration
- SOC 2 Sort II Knowledge Safety and Privateness
- PCI-DSS Data safety

