With knowledge breach occurring at an alarming charge, knowledge safety has grow to be a crucial concern for organizations worldwide.
Do you know?
As per the 2022 IBM Safety Information Breach Report, there was a major improve in the price of knowledge breaches in India, reaching an all-time excessive of Rs 17.6 crore on common for the fiscal 12 months 2022. This quantity is roughly equal to Rs 175 million or $2.2 million.
With such alarming statistics, making certain your group is provided with the precise knowledge safety measures and instruments is extremely important.
To assist IT professionals shield their group’s delicate knowledge and adjust to related rules, now we have created this complete information. It is going to give you an introduction to knowledge safety and help you in understanding the:
- Fundamentals of information safety
- Forms of knowledge safety measures
- Challenges of information safety confronted by IT managers
- Methods for implementing the precise set of information safety applied sciences
Following this information can higher shield your group from any potential knowledge breach incidents.
So, let’s enter the world of information safety collectively by first understanding:
Part 1: What’s Information Safety
The idea of information safety and its significance
Information safety protects knowledge from :
- Unauthorized entry
- Disclosure
- Modification
- Destruction
It’s a essential side of knowledge expertise (IT) and performs an important function in making certain the:
- Confidentiality
- Integrity
- Availability of information for a corporation
Information safety is vital for a number of causes, together with:
1) Defending Confidential Info
2) Compliance with Laws
3) Constructing Buyer Belief
4) Lowering Prices by Minimizing Information Theft
5) Minimizing the Danger of Cyberattacks and Information Breaches
Classifying Information Breaches: An Overview of the Numerous Varieties
1) Malware assaults: Malware is malicious software program that may infect a pc system and steal or harm knowledge. Examples of malware embrace viruses and ransomware.
2) Password assaults: Password assaults contain cracking weak passwords and utilizing stolen passwords to achieve unauthorized entry to a system or community.
3) Insider threats: Insider threats contain staff or contractors who’ve licensed entry to delicate data however misuse it for private acquire or inadvertently trigger a knowledge breach.
4) Phishing assaults: Cybercriminals trick customers into freely giving delicate data by way of faux emails, texts, or web sites.
5) Unsecured IoT Units – Web of Issues (IoT) units that lack correct safety may be exploited by hackers to get entry to a community.

Now, let’s delve deeper into the
Part 2: Complying With Laws
Information Safety Laws: An Overview
Information safety rules are in place to make sure that a corporation’s programs and networks are safe from unauthorized entry or use.
These rules can range by:
However they often embrace necessities for implementing knowledge safety measures and applied sciences and reporting incidents once they happen.
Among the main rules associated to knowledge safety embrace:
1) The Normal Information Safety Regulation (GDPR)
This regulation applies to all companies that deal with the private knowledge of EU residents. It units pointers for :
- Amassing
- Processing
- Storing private knowledge
2) Federal Info Safety Administration Act (FISMA)
This regulation applies to all federal companies inside the USA and units pointers for:
- Managing
- Defending
- Monitoring their data programs
3) The Info Expertise Act, 2000
This Act applies to all companies in India that deal with digital data and units pointers for securing their programs and networks.
The act goals to facilitate:
The act was amended in 2008 to deal with:
- Information safety
- Privateness
- Cyber safety points.
Now let’s perceive
Penalties of failing to adjust to the above knowledge safety rules
1)The Normal Information Safety Regulation (GDPR)
Failure to adjust to GDPR may end up in important fines and penalties.
Organizations may be fined as much as 4% of their world annual income or €20 million.
The corporate’s popularity will also be broken, resulting in:
- Lack of enterprise and prospects
- Discount in income
2) Federal Info Safety Administration Act (FISMA)
Failure to adjust to FISMA may end up in:
- Monetary penalties
- Suspension or revocation of presidency contracts
- Injury to an company’s popularity
3) The Info Expertise Act, 2000
Failure to adjust to this act may end up in:
- A superb (as much as Rs 5 lakh) and/or
- Imprisonment (as much as 3 years)
It might probably additionally result in enterprise loss, popularity harm, and lack of ability to take part in authorities contracts.
Now let’s check out
Prime Firms Information Breach Fines, Penalties, and Settlements
1) Didi World
 Didi World, a Chinese language ride-hailing firm, has been fined $1.19 billion by the Our on-line world Administration of China for violating the:
Didi World, a Chinese language ride-hailing firm, has been fined $1.19 billion by the Our on-line world Administration of China for violating the:
- Nation’s community safety
- Information safety
- Private data safety legal guidelines
Didi World has accepted the choice after a year-long investigation into its safety practices and suspected unlawful actions.
2) Amazon
 Luxembourg fined Amazon €746 million ($877 million) for GDPR violations associated to cookie consent in the summertime of 2021.
Luxembourg fined Amazon €746 million ($877 million) for GDPR violations associated to cookie consent in the summertime of 2021.
Amazon appealed the superb, stating that there was no knowledge breach or publicity of buyer knowledge to any third celebration.
3) Instagram
 Instagram was fined by Eire’s Information Safety Commissioner in September 2022 for violating youngsters’s privateness beneath GDPR, particularly relating to minors’ telephone numbers and e mail addresses being uncovered by way of the platform’s analytics instruments.
Instagram was fined by Eire’s Information Safety Commissioner in September 2022 for violating youngsters’s privateness beneath GDPR, particularly relating to minors’ telephone numbers and e mail addresses being uncovered by way of the platform’s analytics instruments.
4) Meta (Fb)
 The Irish DPC fined Meta €265 million for compromising 500 million customers’ private data.
The Irish DPC fined Meta €265 million for compromising 500 million customers’ private data.
The inquiry centered on Fb, Messenger, and Instagram instruments and compliance with GDPR obligations.
5) Uber
 Uber had a large knowledge breach in 2016, affecting 57 million customers and 600,000 drivers.
Uber had a large knowledge breach in 2016, affecting 57 million customers and 600,000 drivers.
As an alternative of reporting it, they paid $100,000 to maintain it quiet. In 2018, they have been fined $148 million for breaking knowledge breach notification legal guidelines.
Now that you’ve an understanding of the fundamentals of information safety let’s check out
Revolutionary Options To Information Safety Challenges For IT Managers
1) Lack of visibility
With out precise visibility into the information flows and processes, it may be troublesome for companies to make sure how staff are accessing and utilizing firm knowledge.
This lack of visibility can result in:
- Information Breach
- Unauthorized Entry
- Information Leakage
Resolution 1) Choosing worker monitoring software program
Putting in worker monitoring software program can present visibility into how staff use firm knowledge and be certain that potential dangers are recognized rapidly.
![]() The software program may also assist:
The software program may also assist:
- Detect potential malicious actions
- Observe URL visited and app utilization
- Monitor shared assets
- Observe entry to confidential data
This helps companies adjust to rules and forestall knowledge breaches by offering the mandatory visibility, monitoring, and prevention capabilities to guard delicate knowledge.
2) Elevated danger of insider threats & lack of accountability
As firms undertake cloud applied sciences and distant work, the chance of insider threats has elevated.
This may be attributable to a scarcity of accountability and monitoring of staff with delicate knowledge entry. This may result in :
- Information manipulation
- Unauthorized entry
- Theft of company knowledge and mental property
Resolution 2) Use real-time Screenshot capturing software program
Actual-time screenshot-capturing software program may also help companies proactively detect and forestall insider threats by offering visibility on how staff use company knowledge.
The software program additionally permits groups to observe worker actions, resembling:
- Taking screenshots of consumer actions at specified intervals
- Monitoring distant desktop actions
- Recording keystrokes and mouse actions
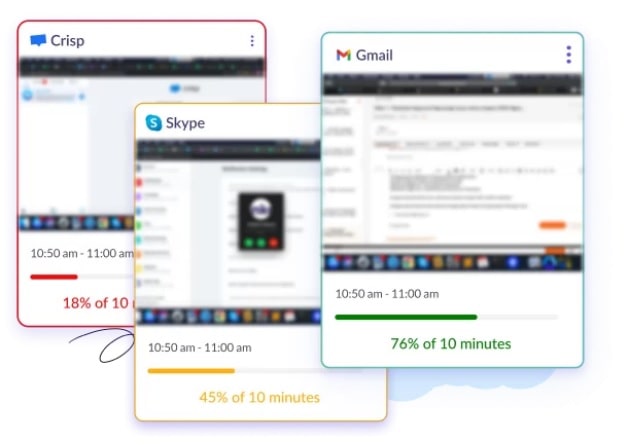 This helps establish potential insider threats and holds staff accountable for his or her actions, which may cut back the chance of malicious conduct.
This helps establish potential insider threats and holds staff accountable for his or her actions, which may cut back the chance of malicious conduct.
Problem 3: Gradual incident response
Organizations want to have the ability to reply rapidly and effectively to a knowledge breach or different safety incident.
However this may be troublesome if they don’t have real-time reviews of safety incidents resulting in:
- Delayed response time
- Elevated harm to delicate knowledge
- Popularity harm
Resolution 3) Use real-time alerting and reporting software program
Actual-time alerting and reporting software program may also help organizations detect and reply to safety incidents rapidly by producing reviews resembling:
- Time & Exercise Report
- Weekly Report
- App & URL Reviews
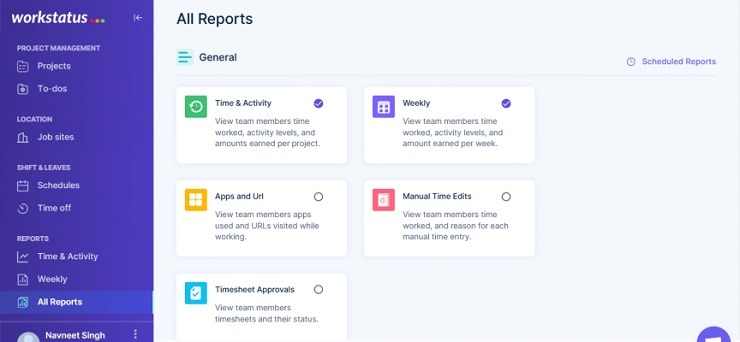 These reviews can present visibility into potential threats, enabling IT personnel to:
These reviews can present visibility into potential threats, enabling IT personnel to:
- Quickly establish
- Mitigate
- Resolve the incident
Problem 4: Particular person authentication-
As organizations prolong entry to extra customers and exterior sources, it may be troublesome for IT personnel to confirm a person’s identification.
It might probably result in:
- Unauthorized entry to delicate knowledge
- Elevated danger of malicious actions
- Information breaches attributable to consumer impersonation
Resolution 4) Use attendance with selfie administration software program
Attendance with selfie administration software program may also help organizations confirm a person’s identification and be certain that solely licensed personnel have entry to delicate knowledge.
The software program makes use of facial recognition expertise to confirm the identification of staff and exterior customers earlier than granting entry to firm assets.
This reduces the chance of:
- Unauthorized entry
- Malicious actions
- Information breaches attributable to consumer impersonation
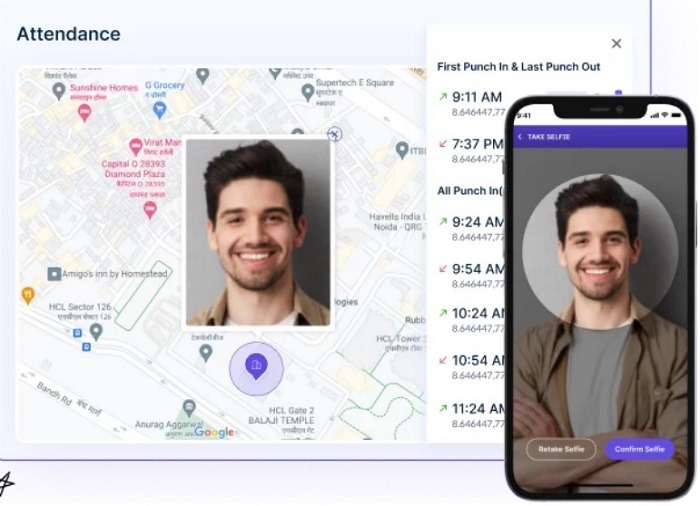 Moreover, the software program can:
Moreover, the software program can:
Making it simpler for organizations to adjust to labor rules and be certain that staff work as required.
So these have been the widespread challenges confronted by IT managers and the revolutionary options which can be utilized to beat these challenges.
Now, the primary query is the place to begin in relation to implementing knowledge safety measures.
That is the place the Workstatus is available in.

Workstatus is an worker monitoring software program that may assist organizations on this regard. It supplies real-time visibility into:
- Worker actions
- Actual-time operations
- Utilization of functions
With Workstatus, IT professionals can:
- Monitor worker actions
- Observe web site visits & app utilization
- Analyze productiveness
- Guarantee knowledge safety
- Safe confidential data
Serving to firms shield their group’s delicate knowledge and adjust to related rules.
So, there you could have it, a complete information to knowledge safety.
Subsequent step
In conclusion, knowledge safety is a crucial side of any enterprise and will by no means be neglected.
Firms that fail to implement efficient safety measures are prone to knowledge breaches, which may result in:
- Important monetary losses
- Lack of belief from prospects
- Authorized liabilities
Subsequently, it’s essential to adjust to related rules and undertake sturdy safety measures to stop knowledge breaches.
As a primary step, you’ll be able to go for Workstatus, the all-in-one platform that gives superior knowledge security measures to guard your knowledge.
So don’t wait till a knowledge breach occurs to take motion.
Shield your small business right this moment with Workstatus.
Join a free trial now and expertise peace of thoughts figuring out your knowledge is safe.
Thanks for studying!
FAQs
Q: What ought to I do if a knowledge breach happens?
A: If a knowledge breach happens, it is best to
- Instantly notify the affected people and authorities
- Trigger and scope of the breach
- Comprise the harm and forestall additional entry
- Implement measures to stop future breaches
Q: How can I guarantee compliance with knowledge safety rules?
A: To make sure compliance with knowledge safety rules, it is best to
- Conduct common danger assessments (utilizing monitoring software program)
- Develop and implement safety insurance policies and procedures
- Practice staff on safety consciousness
- Implement technical and administrative controls
- Usually audit and report compliance
Q: What are another instruments to stop knowledge breaches?
A: To forestall knowledge breaches, you’ll be able to implement a mixture of technical controls, resembling
- Firewalls
- Antivirus software program
- Intrusion detection programs
Administrative controls, resembling
- Safety insurance policies
- Danger assessments
- Incident response plans

