Safeguarding enterprise knowledge has turn out to be a paramount concern for organizations worldwide.
With the rising reliance on evolving applied sciences, there’s a rising want to handle the fashionable considerations surrounding knowledge safety, corresponding to:
- Insider Threats
- Information Loss or Leakage
- Unauthorized Entry
- Productiveness Loss
- Mental Property Theft
Additionally, greater than 51% of firms don’t have any incident response (IR) plan prepared for responding to knowledge breaches and cyber-attacks. [SMB Cybersecurity Report, 2021]
Nevertheless, with worker monitoring instruments like Workstatus, you may put together a fast response plan primarily based on the monitored sample and knowledge. Thus, serving to you to:
- Detect and stop knowledge breaches
- Mitigate insider threats
- Guarantee compliance
- Promote a productive work atmosphere
 This weblog explores the significance of efficient worker monitoring options in guaranteeing the safety and integrity of your corporation knowledge.
This weblog explores the significance of efficient worker monitoring options in guaranteeing the safety and integrity of your corporation knowledge.
Allow us to discover worker monitoring options and uncover how they can assist safeguard your most useful asset: your knowledge.
Understanding Worker Monitoring
Worker monitoring is essential for firms searching for to guard their beneficial knowledge belongings.
Monitoring instruments enable you to realize insights into worker actions, detect potential dangers, and guarantee compliance with knowledge safety rules.
For instance, within the monetary {industry}, monitoring software program can assist forestall unauthorized entry to delicate buyer data.
Equally, in healthcare, monitoring instruments can help in sustaining HIPAA compliance and safeguarding affected person knowledge.
 And IT can forestall unauthorized entry to confidential shopper knowledge and mental property, guaranteeing the safety and integrity of its beneficial belongings.
And IT can forestall unauthorized entry to confidential shopper knowledge and mental property, guaranteeing the safety and integrity of its beneficial belongings.
By monitoring worker actions, you may proactively establish and deal with potential safety breaches and safeguard knowledge from unauthorized disclosure or misuse.
See the facility of Workstatus in motion
Shield your knowledge, improve productiveness, and optimize operations
Enroll Now!
Shield Your Information with Workstatus
Workstatus is an AI-powered worker monitoring software program designed to empower organizations with:
- Higher ROI
- Improved knowledge safety
- Streamlined operations
 With its strong options and intuitive interface, Workstatus allows organizations to realize beneficial insights into worker actions, observe time, and guarantee compliance with knowledge safety rules.
With its strong options and intuitive interface, Workstatus allows organizations to realize beneficial insights into worker actions, observe time, and guarantee compliance with knowledge safety rules.
By leveraging Workstatus, you may proactively:
- Tackle potential dangers
- Detect insider threats
- Optimize useful resource allocation
With its user-friendly design and highly effective capabilities, Workstatus is the perfect resolution for organizations searching for to reinforce productiveness, defend delicate knowledge, and foster a safe work atmosphere.
Right here’s what you are able to do with the Workstatus:
1. Web and App Monitoring
![]()
- Achieve visibility into web utilization and app actions to make sure compliance and stop unauthorized entry to delicate data.
- Monitor and analyze the web sites and functions workers are utilizing to establish potential safety dangers or any insider threats.
- Set customizable restrictions or alerts to stop workers from accessing inappropriate web sites or utilizing unauthorized functions, guaranteeing a safe work atmosphere.
2. Screenshot Seize
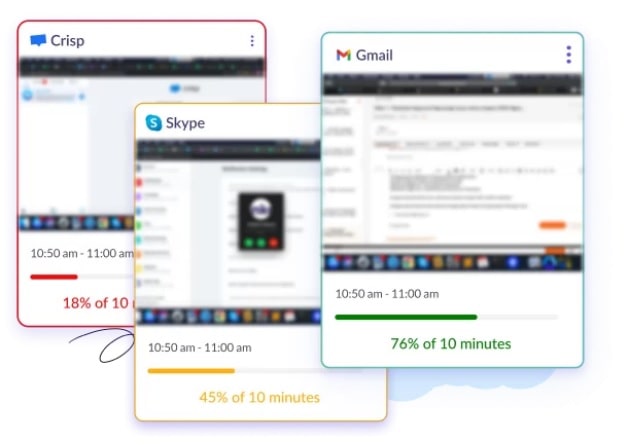
- Seize screenshots at specified intervals to watch worker actions and establish suspicious or unauthorized conduct.
- Use the screenshot characteristic to confirm that workers adhere to firm insurance policies and safety protocols, stopping potential knowledge breaches.
- Achieve insights into worker productiveness and activity progress by reviewing screenshots, enabling higher useful resource allocation and activity administration.
3. Idle Time Tracker
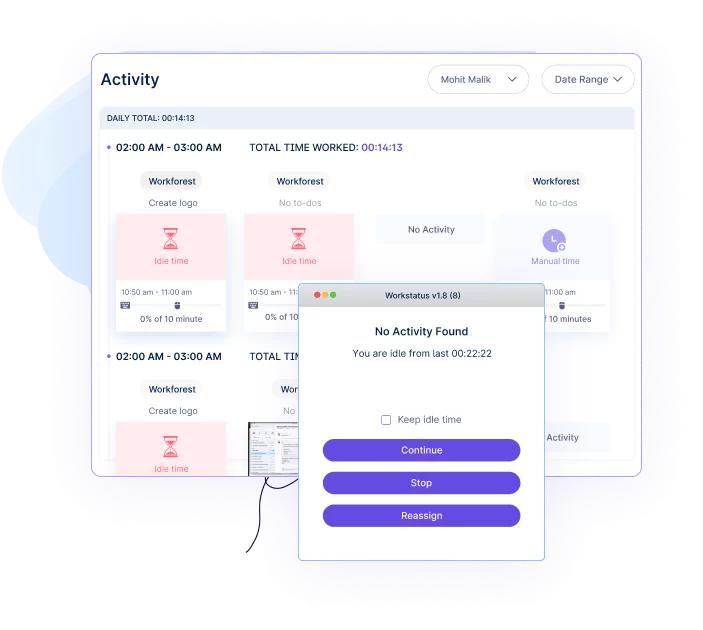
- Monitor idle time and detect situations of extended inactivity, serving to firms establish unproductive conduct and decrease time wastage.
- Enhance worker accountability by highlighting durations of extreme idle time and addressing potential productiveness points.
- Optimize useful resource allocation by understanding when workers could also be experiencing workflow interruptions or system-related delays.
4. Calculate Efficient Time
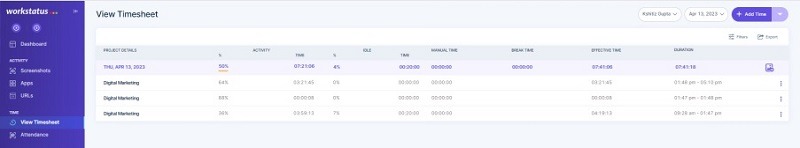
- Differentiate between efficient and wasted time to guage worker effectivity and establish areas for enchancment.
- Decide the time spent on important duties versus non-work-related actions, enabling groups to reinforce productiveness and time administration.
- Implement focused methods, corresponding to coaching or workflow optimization, primarily based on insights gained from monitoring productive and unproductive time.
5. Time & Exercise Reviews
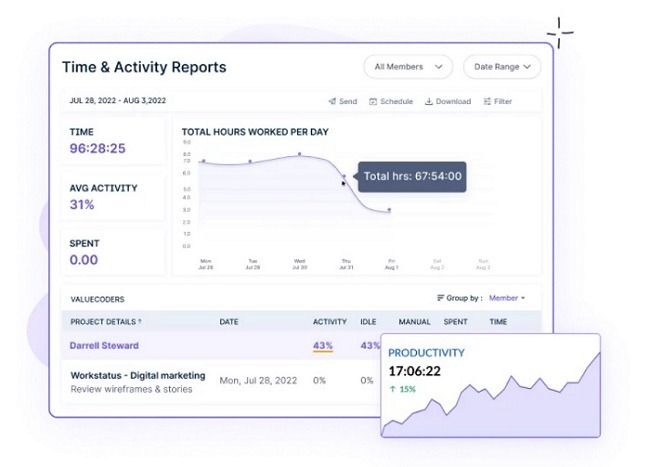
- Generate complete stories detailing worker time logs and exercise breakdowns, offering beneficial knowledge for efficiency analysis and challenge administration.
- Use detailed time stories to precisely invoice shoppers or analyze challenge timelines, enhancing accuracy and transparency in shopper interactions.
- Monitor developments in worker conduct, productiveness, and time allocation over time, enabling managers to make knowledgeable choices and optimize operations.
6. Obtain Cellular Apps
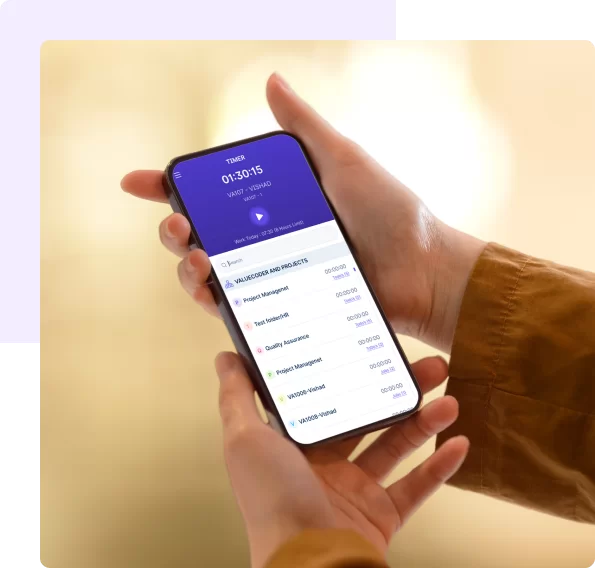
- Entry Workstatus with cellular apps to watch distant or discipline groups effectively.
- Allow real-time monitoring of worker actions, guaranteeing steady knowledge safety and productiveness optimization.
- Seamlessly combine cellular gadgets into the monitoring course of, offering a complete resolution for organizations with a cellular workforce or distant groups.
By using these industry-specific options of Workstatus, you may successfully defend their knowledge, improve productiveness, and guarantee compliance.
Finally resulting in improved operational effectivity and a safe work atmosphere.
Success Tales: Actual-Life Examples
Learn the under infographics to understand how Workstatus protected organizations from time frauds, knowledge breaches, insider threats, and extra.

These success tales, supported by related statistics, reveal the constructive affect of Workstatus throughout varied industries.
Greatest Practices for Maximizing Workstatus
Listed here are some finest practices for knowledge safety whereas utilizing Workstatus:
1. Outline Clear Monitoring Insurance policies
Set up clear and well-defined monitoring insurance policies that clearly talk the next issues for utilizing Workstatus:
- Objective
- Scope
- Expectations
Guarantee workers perceive that monitoring goals to reinforce productiveness and knowledge safety whereas respecting privateness.
2. Customise Monitoring Settings
Tailor Workstatus to your particular wants by customizing monitoring settings.
Alter parameters corresponding to web and app monitoring, screenshot frequency, or idle time thresholds to align along with your necessities and guarantee optimum monitoring effectiveness.
3. Use Information for Steady Enchancment
Often assessment and analyze the information and stories generated by Workstatus to:
- Determine developments
- Areas for enchancment
- Alternatives to reinforce productiveness
Leverage insights from the information to implement focused methods, optimize workflows, and allocate sources successfully.
4. Keep Authorized Compliance
Guarantee compliance with related privateness and knowledge safety rules by implementing and utilizing Workstatus.
Safeguard worker privateness and guarantee knowledge collected is used solely for meant functions.
5. Foster Clear Communication
Foster an open and clear communication tradition surrounding worker monitoring.
Clearly talk the aim and aims of monitoring to workers, emphasizing its position in knowledge safety and efficiency enchancment.
Encourage workers to supply suggestions and deal with any considerations they could have.
6. Present Worker Coaching
Conduct coaching classes to teach workers about Workstatus, its options, and its advantages.
Clarify how monitoring contributes to knowledge safety and productiveness, deal with any considerations, and information on utilizing the software program successfully.
Wish to take management of your knowledge?
Monitor web and app utilization, observe productiveness, and stop knowledge breaches.
Shield your corporation with Workstatus.
FAQs
Ques. Is worker monitoring authorized?
Ans. Sure, worker monitoring is authorized in most jurisdictions as a result of it complies with native legal guidelines and rules. You will need to set up clear monitoring insurance policies and respect worker privateness rights.
Ques. How does Workstatus guarantee worker privateness?
Ans. Workstatus respects worker privateness by offering customizable monitoring settings, specializing in work-related actions, and adhering to privateness rules. It permits organizations to strike a steadiness between knowledge safety and worker privateness.
Ques. Can worker monitoring enhance productiveness?
Ans. Sure, worker monitoring can enhance productiveness by offering insights into time spent on duties, figuring out inefficiencies, and selling accountability. It permits organizations to optimize workflows and allocate sources successfully.
Ques. How does worker monitoring improve knowledge safety?
Ans. Worker monitoring helps defend enterprise knowledge by detecting and stopping insider threats, figuring out unauthorized entry or knowledge breaches, and selling adherence to safety protocols and insurance policies.

